Cyber Awareness
Cyber Awareness (also known as Cyber Hygiene) is a set of knowledge and practices for application to keep both an individual and organization safe from malicious cyber activity.
Our concept is based on the notion that human risk behaviour management in cyberspace is a continuous process in which trainees and instructors alike need to learn and adapt.
The cyber awareness course is an interactive, engaging and effective tool consisting of a training module and two separate test modules to address human risk behaviour in cyberspace.
Course materials are based on real-life based situations to aid in immersion and realism. Participants are asked to react based on their best judgement.
A comprehensive risk profile is provided to each participant upon the completion of a course.

Cyber Awareness (also known as Cyber Hygiene) is a set of knowledge and practices for application to keep both an individual and organization safe from malicious cyber activity.
Trusted by
Our Core Values
Customized Approach
There are no “catch all” cyber awareness courses. Customization is key to success.
Time Efficiency
Time spent on education & trainings is valuable. Risk assessment helps accomplish 2 goals at once.
Continuous Learning
Cyber awareness trainings need a systemic and continuous approach to provide maximal value.
How We Work?
Personality
Non-Technical-Individual topics are assessed here such as the perception of one’s importance in the cyber hygiene, their attitude towards contributing to risk mitigation as well as discipline in applying all of the technical knowledge available.
Organization
Non-Technical-Surrounding topics are assessed here such as general corporate culture regarding the study topic, information management policies and possible shortcuts and exceptions made in important or difficult situations.
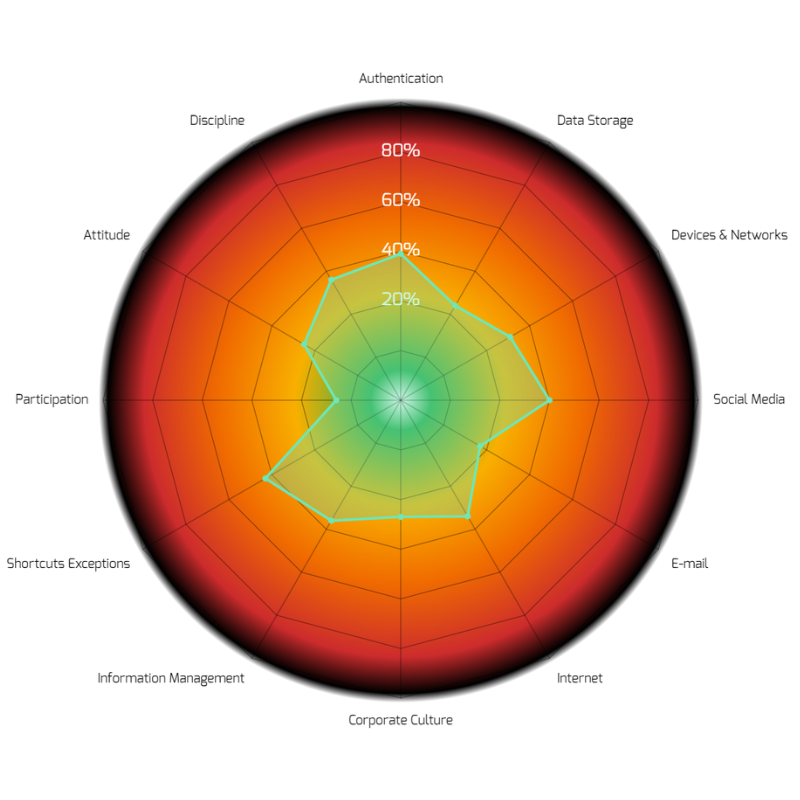
Knowledge
Technical-Individual topics are assessed here such as the concept of passwords (creation & management), multi-factor authentication, data management with external devices and portable or remote working in non-office environments.
Exposure
Technical-Surrounding topics are assessed here such as the influence of social media and its possible threats, phishing via e-mails, segregation of professional & personal e-mail usage as well as safe browsing online.
Technical Specifications








































