Phishing Campaigns
Phishing is becoming a continuous trend and preference of cyber criminals as an attack vector to gain foothold in organisations. Whilst technical systems might be protected with various cybersecurity provisions, penetrating the “human link” of the cybersecurity chain takes only once click.
Protection against different types of phishing attacks requires a certain knowledge base on what to look out for. Whilst phishing campaign simulations are not the most optimal training method, they provide effective measures of assessing your organization’s risk level against real-world attacks.
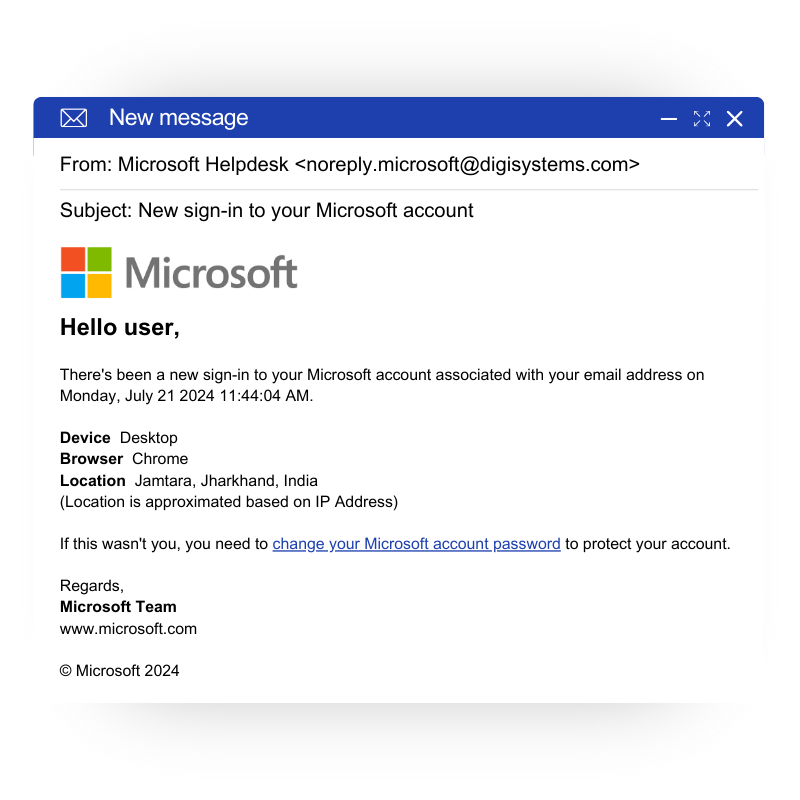
What better way to test your organization’s security against phishing attacks than to have a realistic simulation. Run a fully realistic phishing campaign with customized e-mails and randomized sending with us!

Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers.
Trusted by
Our Core Values
Customized Approach
Phishing campaigns need to be designed according to the target. Customization is key to success.
Time Efficiency
Time spent on education & trainings is valuable. Risk assessment helps accomplish 2 goals at once.
Continuous Learning
Phishing campaigns need a systemic and continuous approach to provide maximal value.
How We Work?
Custom E-mails
Creation of customized e-mails with the help of our experts for the highest level of realism, undetectability and immersion
Randomized Sending
E-mails are sent at randomized intervals to reduce detection and avoid creating patterns
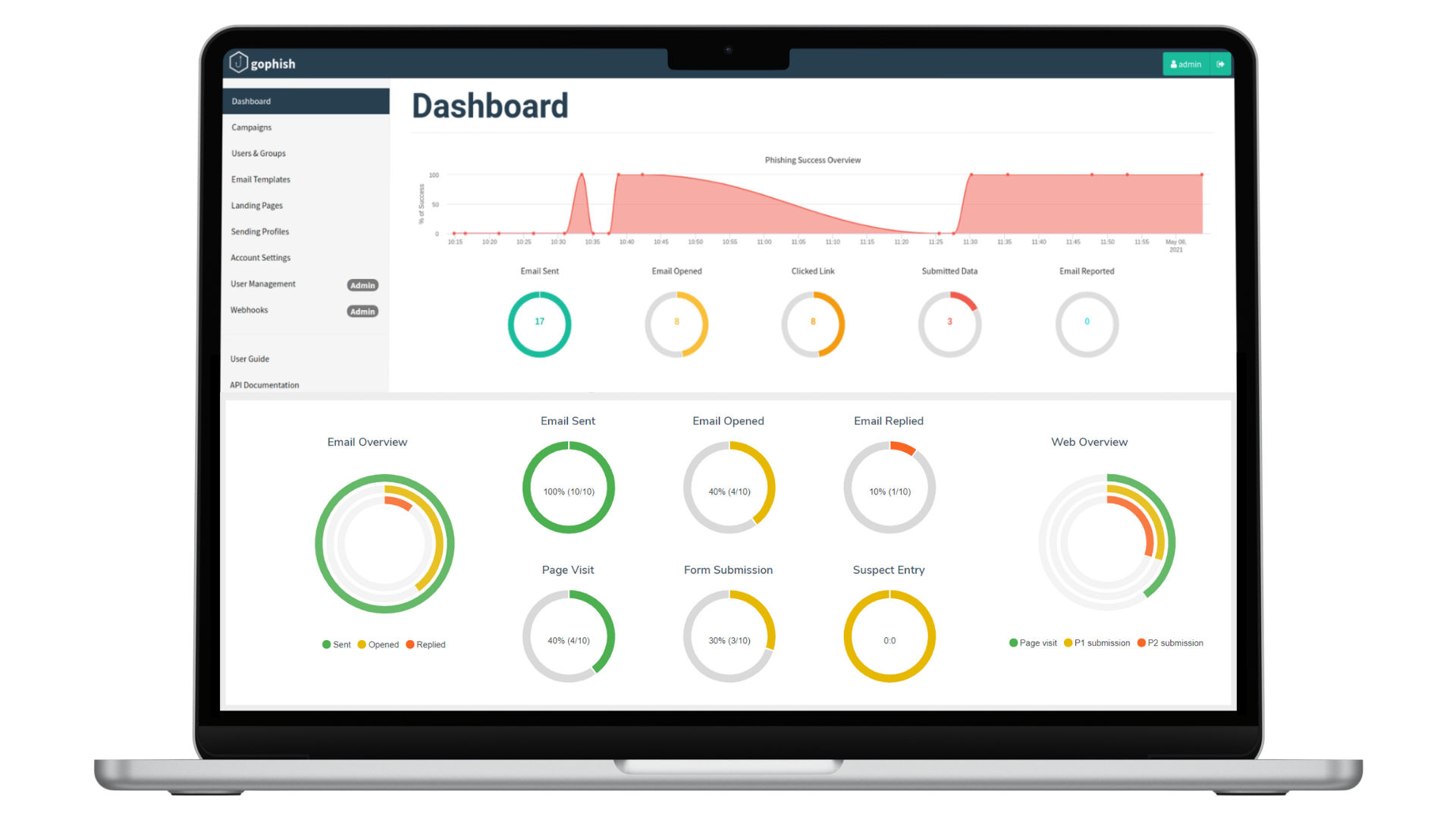
Detailed Tracking & Monitoring
GoPhish offers real-time tracking and monitoring of the campaign in terms of success – clicks, opens, submissions and more
Comprehensive Reporting
Each phishing campaign comes with an analytic report of the progress of the campaign as well as key findings and vulnerabilities
Technical Specifications








































