Cyber Security Awareness
Cyber Security Awareness (also known as Cyber Awareness or Cyber Hygiene) is a set of knowledge and practices for application to keep both an individual and organization safe from malicious cyber activity.
RiskSight’s concept is based on the notion that human risk behaviour management in cyberspace is a continuous process in which trainees and instructors alike need to learn and adapt.
The cyber security awareness e-learning and risk assessment course is an interactive, engaging and effective tool consisting of a training module and two separate test modules designed to educate users on preventing cyber-attacks through proper cyber hygiene, addressing the most common vectors of cyber threats such as social engineering (e.g. phishing attacks), password security and unpatched software.
The course is structured into the following parts:
- Quiz Module: Provides an initial risk assessment benchmark for each individual participant before the learning journey.
- Study Module: Presents real-life scenarios and cases with practical study materials.
- Test Module: Evaluates the accrual and retention of knowledge and skills from the Study Module.
Course materials are based on real-life situations to aid in immersion and realism. Participants are asked to react based on their best judgement enhance user interaction and proactive participation, on the contrary of lengthy standardized reading-heavy texts.
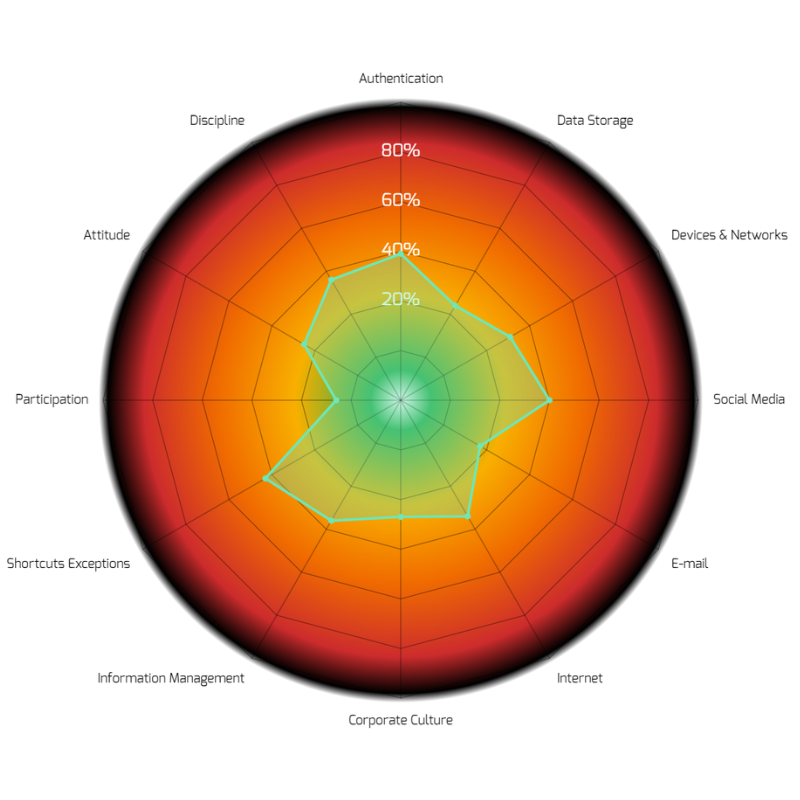
A comprehensive risk matrix is used as the foundation of developing training materials, utilizing a 360-degree security approach that covers both technical and non-technical, individual and environmental (surrounding) threat vectors. A risk profile, relative of the matrix, is provided to each participant upon the completion of the course.

Cyber Security Awareness (also known as Cyber Awareness or Cyber Hygiene) is a set of knowledge and practices for application to keep both an individual and organization safe from malicious cyber activity.
Trusted by
Industries
Cyber Security Awareness Trainings can be conducted both in the Public and Private Sector and are important to all levels of seniority and skills as they provide a baseline level of cyber security maturity required for every IT-systems user.

Public Sector
Public Sector Cyber Security Awareness Trainings generally target broader scope objectives such as government or national cyber awareness maturity, international initiatives or training programs.

Private Sector
Private Sector Cyber Security Awareness Trainings generally focus on business needs in a narrower scope such as enhancing the existing level of cyber awareness and maturity, complying with regulations or international standards.
Use Cases
Cyber Awareness Trainings have numerous use cases which can be applied either standalone or often times in combination, providing the most relevant and actionable data from the user inputs via risk assessment and open-ended feedback.
How We Work?
Personality
Non-Technical-Individual topics are assessed here such as the perception of one’s importance in the cyber hygiene, their attitude towards contributing to risk mitigation as well as discipline in applying all of the technical knowledge available.
Organization
Non-Technical-Surrounding topics are assessed here such as general corporate culture regarding the study topic, information management policies and possible shortcuts and exceptions made in important or difficult situations.
Knowledge
Technical-Individual topics are assessed here such as the concept of passwords (creation & management), multi-factor authentication, data management with external devices and portable or remote working in non-office environments.
Exposure
Technical-Surrounding topics are assessed here such as the influence of social media and its possible threats, phishing via e-mails, segregation of professional & personal e-mail usage as well as safe browsing online.
Dynamic e-Learning and Risk Assessment Platform
RiskSight’s E-Learning and Risk Assessment Trainings are carried out on a proprietary software tool called the Dynamic e-Learning and Risk Assessment Platform (DeLRAP). DeLRAP is a content-agnostic environment where learning and testing activities can be carried out. It provides participants immediate and actionable feedback through interactive case-based learning. This learning and testing process enables consequent auditing and risk assessment on the level of the individual, team, department, the whole organization or any other combination for that matter.
Technical Specifications
Frequently Asked Questions




