
Incident Response Plan: Template & How To Get Started?
What is an Incident Response Plan?
An Incident Response Plan (IRP) is a formally approved document, that is designed to help your organization identify, manage and recover from a cybersecurity incident. Its purpose is to provide a clear framework for identifying and responding to different threats, minimizing damage and recovery time while keeping important assets protected. At its core, an IRP lays out specific steps, roles and protocols to quickly react to and contain incidents.
A well thought out plan is invaluable at uncertain times. With every attack being different and unpredictable, organizations risk disruptions to operation, financial loss and damage to reputation unless the threat is dealt with in an efficient and systematic manner. With every second that is not spent on concrete action towards containment and recovery, the attackers may be burrowing deeper into your network or exfiltrating important data. Figuring out the details of incident response only after an incident has occurred is shortsighted and may lead to greater losses. Why give the attackers a head start?
Key Components of an Incident Response Plan Template
An Incident Response Plan needs several key parts to effectively guide organizations through a cybersecurity incident. These elements ensure that responses are organized, efficient, and focused on minimizing harm.
Preparation. This is all about getting ready before anything happens. It includes training your team, setting up tools, and creating clear policies. Regular practice drills ensure everyone knows their role and how to respond if something goes wrong.
Detection and Analysis. This step is about spotting the problem early and figuring out what’s happening. Monitoring systems and setting up alerts can help catch suspicious activity. Once detected, it’s important to analyze how serious the issue is so you can prioritize your response.
Containment and Eradication. Once the issue is identified, the first step is stopping it from spreading further. Next is eradication, where you remove the cause of the problem. Recovery comes last, ensuring systems and data are safely restored, and everything is back to normal.
Lessons Learned. After handling the incident, reviewing what happened is crucial. This helps identify what went well and what could be improved. Updates to the plan based on these insights prepare the organization for possible future incidents.
NB! Templates are a great starting point for building an IRP, but they should be customized to fit your organization’s needs. Aligning with standards like NIST or ISO ensures your plan meets industry requirements and is ready for audits or compliance checks. Read more about NIST, ISO and other standards from one of our previous posts.
Getting Started with Cyber Incident Response
Getting started with Cyber Incident Response requires preliminary scoping of the organization, its assets and services, key personnel, existing procedures and numerous other considerations. As there is not a “catch all” Incident Response Plan, organizations should tailor their IRPs according to their context. Regardless, there are several key components that are universal to each Incident Response Plan:
Roles and Responsibilities
At minimum roles and responsibilities should be assigned and divided at least across incident management, technology management and communications management areas.
- For incident management itself, the most important aspect is that a specific person spearheads the resolution of each incident.
- For technology management, the most important aspect is that a specific person spearheads the utilization and remediation of technology and systems.
- For communications management, the most important aspect is that a specific person spearheads all communications related to the specific incident.
Each of the areas can have several additional managers, specialists or regular employees, each tending to a specific function under that area depending on the sector, size and nature of the organization.
Identified Threat Scenarios
Based on organizational risk assessments, you should identify key threat scenarios sin order to prepare by tailoring direct response plans to those threats. Having pre-planned threat scenarious greatly decreases the level of confusion and uncertainty in the midst of an impactful cyber-attack.
Testing and Updating
An Incident Response Plan is never complete and is gradually changing in time. As new threats emerge, organizations restructure and people change, the Incident Response Plan needs to be constantly updated and furthermore, practiced to utilize its effectiveness to the utmost degree. A great way to test the effectiveness of an IRP is through tabletop exercises. Tabletop exercises are scenario-based simulations and discussions that focus on improving a company’s cybersecurity decision making in high-stress situations. Learn more about RiskSight’s approach to tabletop exercises.
Leveraging a Cyber Incident Response Checklist
A cyber incident response checklist serves as a vital tool for organizations to navigate the chaos of a cybersecurity incident effectively. This structured approach ensures no critical steps are overlooked, enabling rapid and thorough responses to minimize damage and recovery time. This checklist should be printed out and shared with the key stakeholders related to incident response and business continuity. In addition to being kept in a computer, server or shared drive, physical paper copies are recommended due to possible inaccessibilities to digital systems in the case of a cyber-attack.
Here is a sample checklist with ENISA’s inputs, but there are several online resources available from experts at Delinea, Crowdstrike and government sites. Every template varies in both horizontal and vertical scope and therefore should only be leveraged as a baseline, depending on your organizational needs and peculiarities.
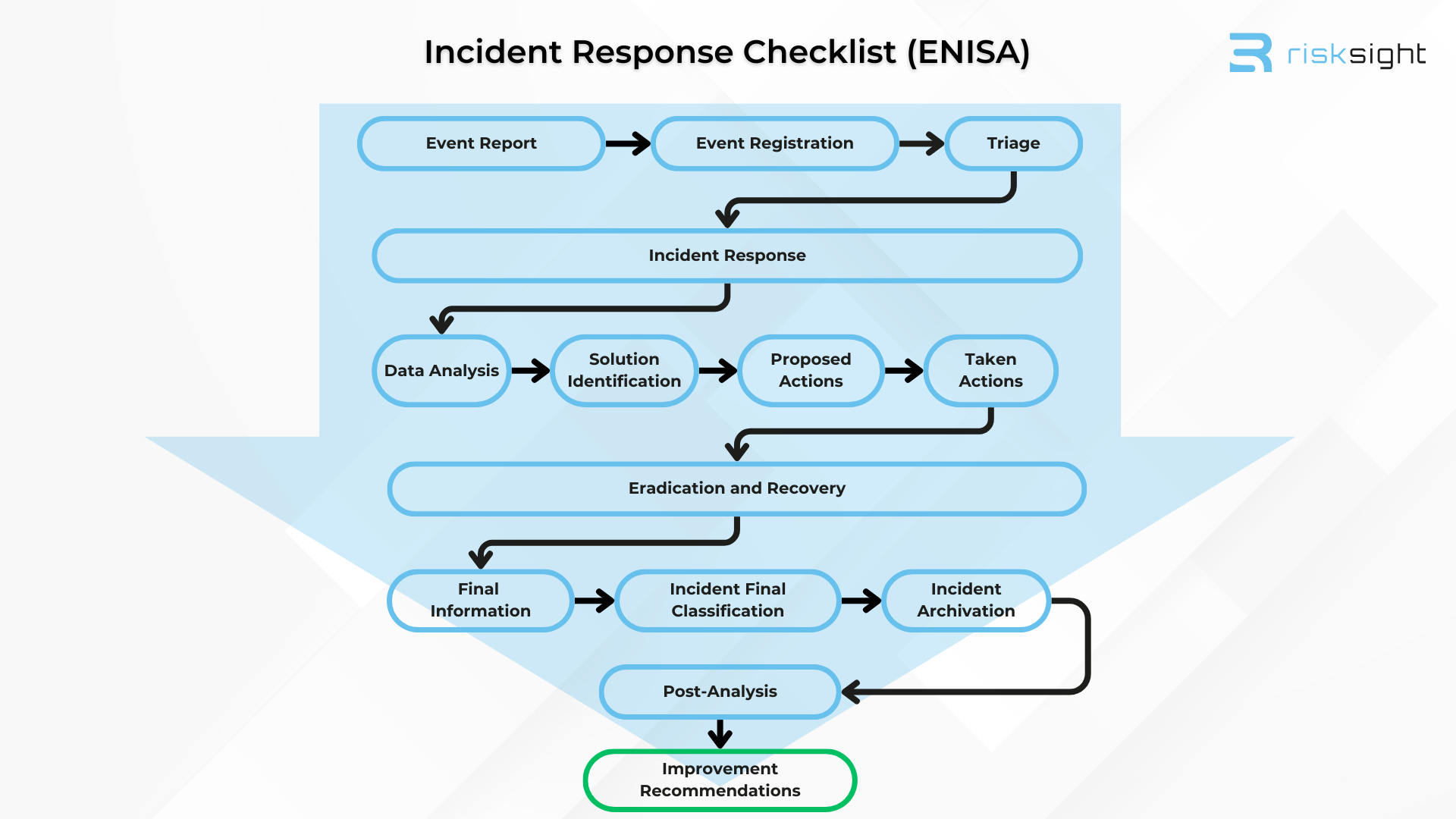
Furthermore, provided down below are some key pillars to focus on in terms of the Incident Response Process.
Situation Assessment
- Confirmation of the Incident
- Initial Triage (Cyber-Attack, IT-Incident etc.)
- Impact on Business Processes and IT-Systems
First Response
- Initiation of Constant Documentation
- Notification and Assembly of Key Stakeholders
- Initiation of Immediate Defensive Measures for Damage Limitation and Analysis Preparations
Situation Analysis and Stabilization
- Creation of Shared Situational Awareness
- Decision-Making Based on Consequence Analysis
- Activation of Business Recovery Measures
Final Documentation
- Final Written Formulation of Taken Actions, Identified Problems and Other Related Decisions
- Highlighting of New Risks, Vulnerabilities or Other Considerations
Summary and Assessment
- Validation of Successful Recovery Measures
- Conduct of a Summary Analysis
- Lessons Identified, Improvement of Business Recovery Measures
