NIS2 Cybersecurity Exercises
With the implementation of the NIS2 Directive, all European Member States must comply with different cybersecurity requirements, a large portion of it related to trainings and exercises.
RiskSight has developed a specific NIS2-focused cybersecurity exercise that is able to cover 8 of the 10 new minimum measures required under the NIS2 Directive, including risk assessments, policies and procedures for evaluating the effectiveness of security measures, a plan for handling security incidents, a plan for managing business operations during and after a security incident and others.
With key pillars on Risk Management, Corporate Accountability, Reporting Obligations and Business Continuity, regular exercising through Strategic Cybersecurity Exercises allows for compliance and continuous improvement of the cybersecurity capacities within an organization.

RiskSight has developed a specific NIS2-focused cybersecurity exercise that covers 8 of the 10 new minimum measures required under the NIS2 Directive.
Trusted by
Industries
The NIS2 Directive affects entities categorized as essential or important for the European economy and society. The division and classification of entities is the following:

Essential Entities (EE)
Size threshold: varies by sector, but generally 250 employees, annual turnover of € 50 million or balance sheet of € 43 million

Important Entities (IE)
Size threshold: varies by sector, but generally 50 employees, annual turnover of € 10 million or balance sheet of € 10 million
Compliance Areas
RiskSight’s NIS2 Cybersecurity Exercise covers several of the required compliance areas indicated in the NIS2 Directive. Through the overarching four pillars of Risk Assessment, Corporate Accountability, Reporting Obligations and Business Continuity, the measures in compliance are:
How We Work?
Scenario-Based Exercise
Each exercise is conducted via a fictitious scenario based on past real-life events and incidents to provide realism and interaction.
Division of “Substantive” & “Framework” issues
Often times decision themselves are easier to make than the necessary aspects agreed upon beforehand to make them. Hence, the division of “substantive” and “framework” issues is a vital tool to exercise success.

Instant Results Visualization
The STRATEX Software offers instant capturing and visualization of Exercise results, facilitating fruitful discussions and opinions.
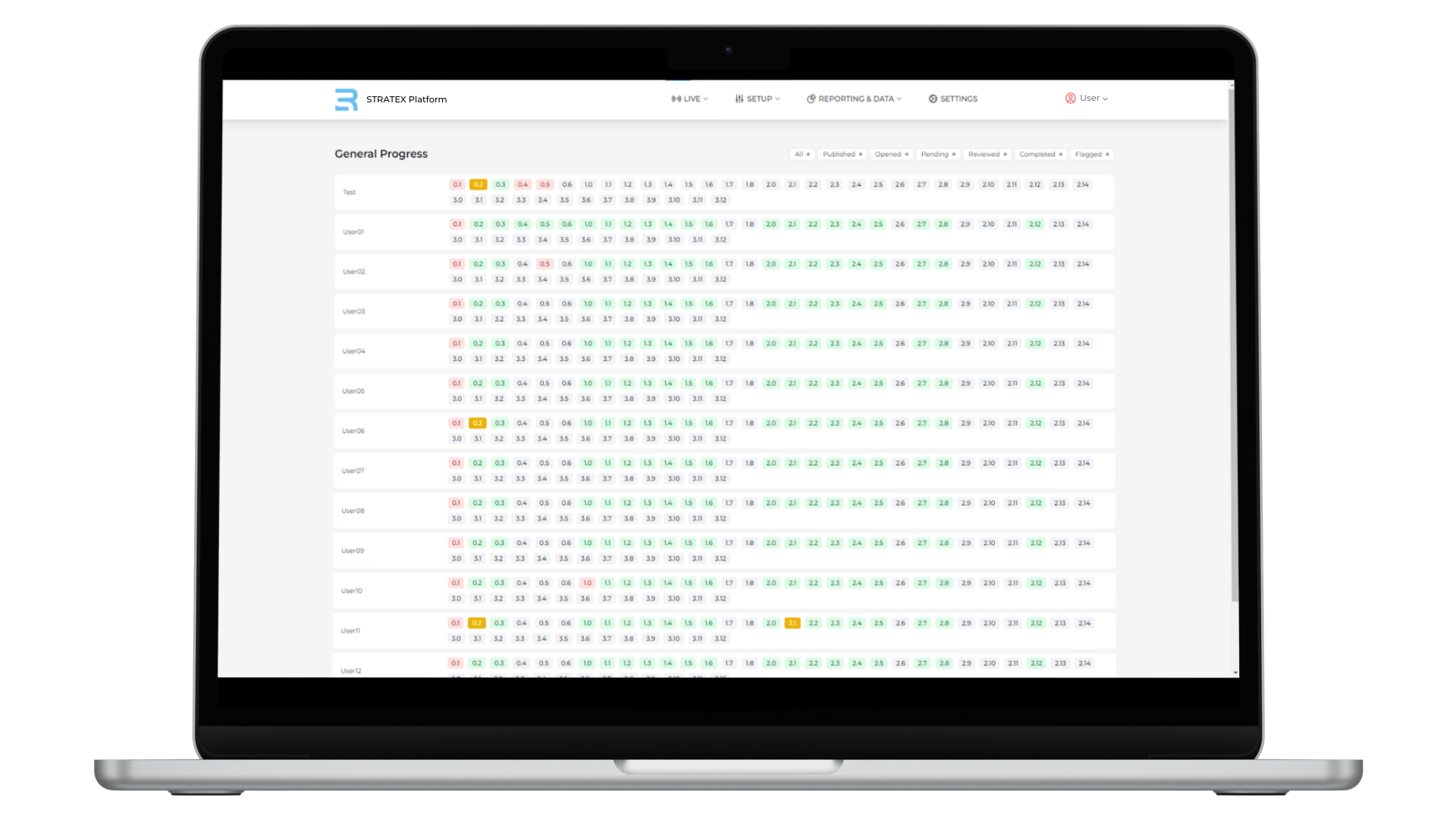
Comprehensive Progress Management
The STRATEX Software allows exercise management personnel to comprehensively monitor and manage the exercise progress, guaranteeing a timely and problem free execution.
STRATEX Platform
RiskSight’s Strategic Cybersecurity Exercises are carried out on a proprietary exercise management tool called the STRATEX Platform. The tool is highly scalable, very intuitive to use and can simultaneously support a large number of participants across the globe. The tool has an effective and instant feedback module that makes it engaging not only to participants but also observers. Its data capture functionalities ensure that Exercise discussions will not be lost and can be used for later in-depth analysis. The Exercise is usually accompanied by a feedback session where main events, decisions and reactions are analyzed. This ensures participant engagement and truly effective learning experience.
Technical Specifications




