Risk Assessment Methodology
Our Risk Assessment Methodology is based on a simple 2-axis model consisting of 4 main categories.
The vertical axis splits content into non-technical and technical categories, whilst the horizontal axis splits content into individual and surrounding categories. On the basis of this, the categories created are the following:
- Technical Individual
- Technical Surrounding
- Non-Technical Surrounding
- Non-Technical Individual
This risk assessment methodology has been adapted for our cyber awareness (cyber hygiene) and compliance (data protection, anti-corruption and business ethics and anti-money laundering) courses but can be used regardless of industry and study topics, being proven in various other contexts such as forestry, disinformation, educational emergency provisions and more.

Our Risk Assessment Methodology is based on a simple 2-axis model consisting of 4 main categories.
Risk Matrix Categories

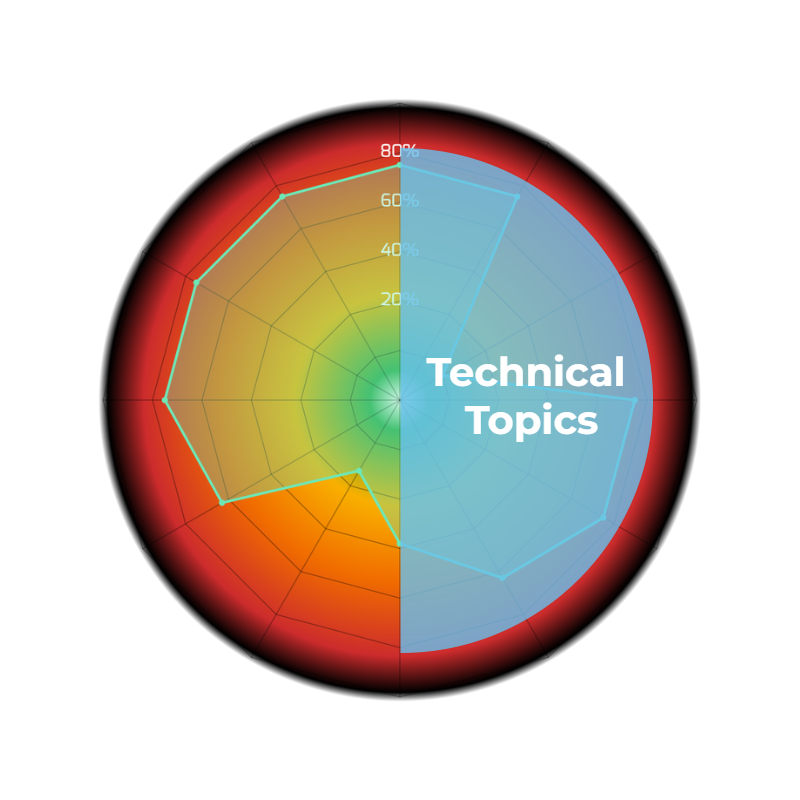


The left half of the risk radar consists of purely non-technical topics. These topics are based on non-technical takes such as attitude and organizational behaviour, which are often times difficult to impact. These topics consist of both individual and surrounding elements.
The right half of the risk radar consists of purely technical topics. These topics are based on technical knowledge and can be taught to the trainee completing the course. These topics consist of both individual and surrounding elements.
The upper half of the risk radar consists of individual topics. These topics are exclusively related to the trainee completing the course. These topics consist both of non-technical and technical elements.
A Single Framework to Cover All Risks
Non-Technical Individual
Threats and attack vectors that represent the individuals personal take on the domain and topics at hand
Non-Technical Surrounding
Threats and attack vectors that represent the organization the individual is figuring in
Technical Individual
Threats and attack vectors that come from the technical elements the individual uses personally in day to day activities
Technical Surrounding
Threats and attack vectors that come from the surrounding technical environment the individual is exposed to




